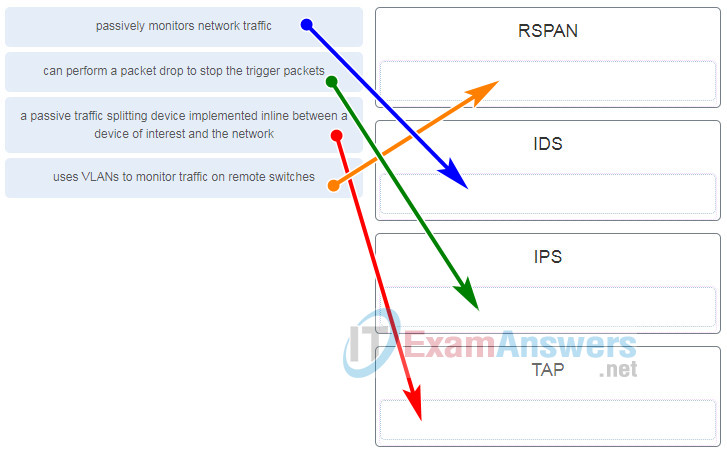
44 identify and label the following attacks by dragging the term on the left to the definition on the right. not all terms are used.
CISSP Attack Types Flashcards a form of network attack in which a valid data transmission is maliciously or fraudulently repeated with the goal of obtaining unauthorized access. Term. Replay Attack. Definition. an attacker capturing the traffic from a legitimate session and replaying it to authenticate his session. Term. session hijacking. Definition. If an attacker can ... Foot drop - Symptoms and causes - Mayo Clinic Jan 5, 2023 · Foot drop is caused by weakness or paralysis of the muscles involved in lifting the front part of the foot. Causes of foot drop might include: Nerve injury. The most common cause of foot drop is compression of a nerve in the leg that controls the muscles involved in lifting the foot. This nerve is called the peroneal nerve.
B1 Preliminary vocabulary list - Cambridge English The meaning of each word or phrase in the wordlists has been assigned ... Not all the words in the Topic Lists headings appear on the wordlist.

Identify and label the following attacks by dragging the term on the left to the definition on the right. not all terms are used.
Answers - Pearson Book spread 7Ad Cells. There should not be any chloroplasts shown. The following should be labelled: nucleus, cytoplasm, vacuole, cell surface. Solved Drag each label into the appropriate position to - Chegg Expert Answer. Drag each label into the appropriate position to identify which joint is being described. Hip Arterial damage entering the fovea capitis can result in necrosis Acetabular labrum increased the depth of the socket Tibiofemoral joint Knee Inversion sprains produce damage to the lateral ligaments to the tibiai collateral ligament ... Identify and label the following attacks by dragging the term ... MasqueradingMasquerading An attacker pretending to be from a trusted organization sends emails to senior executives andAn attacker pretending to be from a trusted organization sends emails to senior executives and high-profile personnel asking them to verify personal information or send money.high-profile personnel asking them to verify personal …
Identify and label the following attacks by dragging the term on the left to the definition on the right. not all terms are used.. Solved Part A - Components of Reflex Pathways Assign each - Chegg Question: Part A - Components of Reflex Pathways Assign each term to the appropriate definition by dragging the box into the appropriate compartment Drag the terms on the left to the appropriate blanks on the right to complete the sentences. View Available Hintis Reset Help sensor 1. A (n) results from changes in organ activity. Answers - Pearson b The food does not contain all the vitamins ... enzymes do not get used up as they carry out ... 2 correct labels from left to right: sex cell; gamete;. CyberSecurity Chapter 3 Flashcards | Quizlet 1)clear and detailed descriptions of penalties if the level of service is not provided 2)detailed provider responsibilities for all continuity and disaster recovery mechanisms You plan to implement a new security device on your network. Which of the following policies outlines the process you should follow before implementing that device? 1.6 Anatomical Terminology - Anatomy and Physiology 2e - OpenStax The sagittal plane is the plane that divides the body or an organ vertically into right and left sides. If this vertical plane runs directly down the middle of the body, it is called the midsagittal or median plane. If it divides the body into unequal right and left sides, it is called a parasagittal plane or less commonly a longitudinal section.
Ideologies of political parties: lesson overview - Khan Academy The definition of liberalism has changed over time, but modern-day liberals tend to believe that government should intervene in the economy and provide a broad range of social services to ensure well-being and equality across society. Liberals usually believe that the government should not regulate private sexual or social behaviors. Correct Correct Identify And Label The Following Attacks By ... CorrectCorrect Identify and label the following attacks by dragging the term on the left to the definition on theIdentify and label the following attacks by dragging the term on the left to the definition on the right. Not all terms are used.right. Not all terms are used. Identify and label the following attacks by dragging - Course Hero Text Preview: Identify and label the following attacks by dragging the term on the left to the definition on the Identify and label the following attacks by dragging the term on the left to the definition on the right. Not all terms are used. right. Not all terms are used. Chapter 21 Immune System Flashcards | Quizlet Study with Quizlet and memorize flashcards containing terms like Indicate whether the label identifies an adaptive or nonspecific form of defense., Complete each sentence regarding inflammation by dragging the proper label into the appropriate position., Classify each item as a first, second, or third line of defense. and more.
Drag and drop the attack-mitigation techniques from the left onto the ... What happens when the route map route-map QUESTION permit 20 does not contain a conditional match statement? A technician is booting a PC that has Windows 10 installed on dynamic drives. The boot process is currently working on the following step: POST. What is the next step that will happen in the boot process? CompTIA Security+ Domain 1: Threats, Attacks and ... - Quizlet When users run the software, it installs itself as a hidden program that has administrator access to various operating system components. The program then tracks system activity and allows an attacker to remotely gain administrator access to the computer. Which of the following terms best describes this software? Rootkit item at position 22 identify and label the following attacks ... Sep 2, 2022 · 1) An attacker deceives staff into granting access to sensitive data or protected systems by posing as someone who needs or is authorized to have that access. Whaling 2) A hacker impersonating a reputable company sends emails to high-profile employees requesting them to confirm personal information or send money. Vishing Chapter 5: Aerodynamics of Flight - Federal Aviation Administration Thrust, drag, lift, and weight are forces that act upon all aircraft in flight. ... words, any time the flight path of the aircraft is not horizontal,.
3.5 Flashcards | Quizlet Identify and label the following attacks by dragging the term on the left to the definition on the right. Not all terms are used. 1) An attacker convinces personnel to grant access to sensitive information or protected systems by pretending to be someone who is authorized and/or requires that access.
Test 1 Flashcards - Quizlet Identify and label the following attacks by dragging the term on the left to the definition on the right. Not all terms are used. ○ Vishing ○ Piggybacking
Test Out 3 - Subjecto.com You identify the following values: • Asset value = 400 ... Identify and label the following attacks by dragging the term on the left to the definition on the right. Not all terms are used. Vishing Piggybacking Spam Phishing Whaling
CISSP exam questions: 5 drag & drop and hotspot questions Before simply dragging and dropping DAC, RBAC and MAC from left to right, though, you would need to pay close attention to the word “NOT” in the question. With ...
Social Engineering: Definition & 6 Attack Types - Tripwire Mar 1, 2023 ... This type of malicious actor ends up in the news all the time. But they're not the only ones making headlines. So too are “social engineers,” ...
Transient ischemic attack (TIA) - Symptoms and causes Causes. A TIA has the same origins as that of an ischemic stroke, the most common type of stroke. In an ischemic stroke, a clot blocks the blood supply to part of the brain. In a TIA, unlike a stroke, the blockage is brief, and there is no permanent damage.. The underlying cause of a TIA often is a buildup of cholesterol-containing fatty deposits called plaques (atherosclerosis) in an artery ...
Table properties | Qlik Sense on Windows Help Data. Click Add column to add a dimension or a measure. Options that are dimmed are not available. Columns. In the table ...
Identify and label the following attacks by dragging the term ... MasqueradingMasquerading An attacker pretending to be from a trusted organization sends emails to senior executives andAn attacker pretending to be from a trusted organization sends emails to senior executives and high-profile personnel asking them to verify personal information or send money.high-profile personnel asking them to verify personal …
Solved Drag each label into the appropriate position to - Chegg Expert Answer. Drag each label into the appropriate position to identify which joint is being described. Hip Arterial damage entering the fovea capitis can result in necrosis Acetabular labrum increased the depth of the socket Tibiofemoral joint Knee Inversion sprains produce damage to the lateral ligaments to the tibiai collateral ligament ...
Answers - Pearson Book spread 7Ad Cells. There should not be any chloroplasts shown. The following should be labelled: nucleus, cytoplasm, vacuole, cell surface.



























Post a Comment for "44 identify and label the following attacks by dragging the term on the left to the definition on the right. not all terms are used."